150+
clients
clients

600+
projects delivered
projects delivered

100+
consultants
consultants
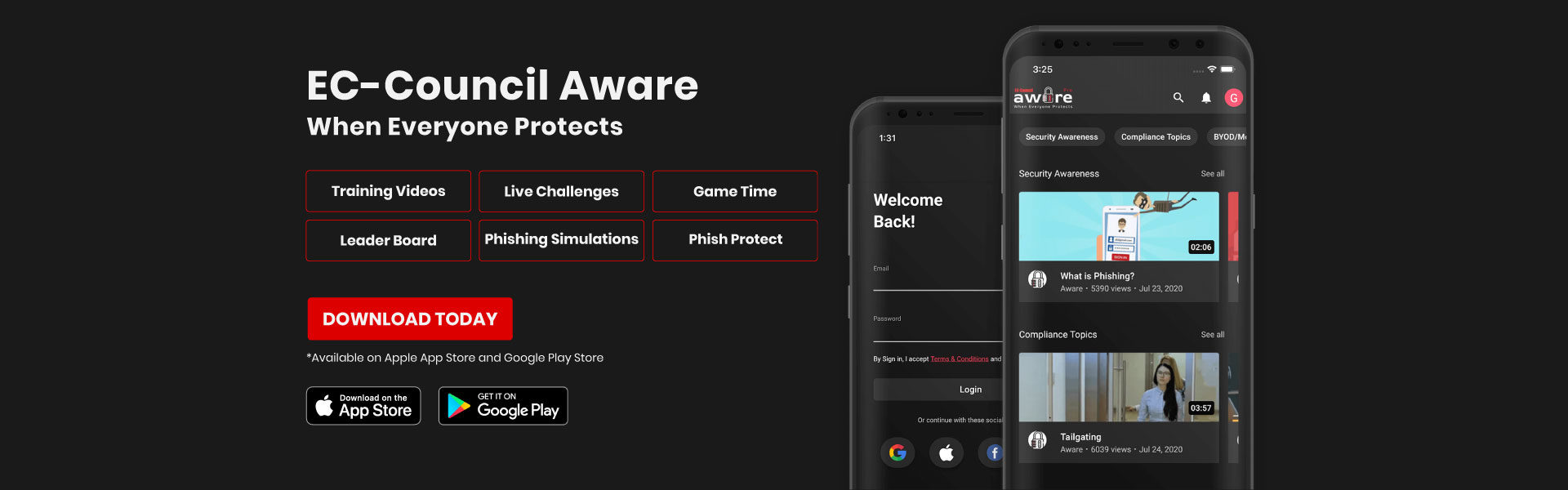
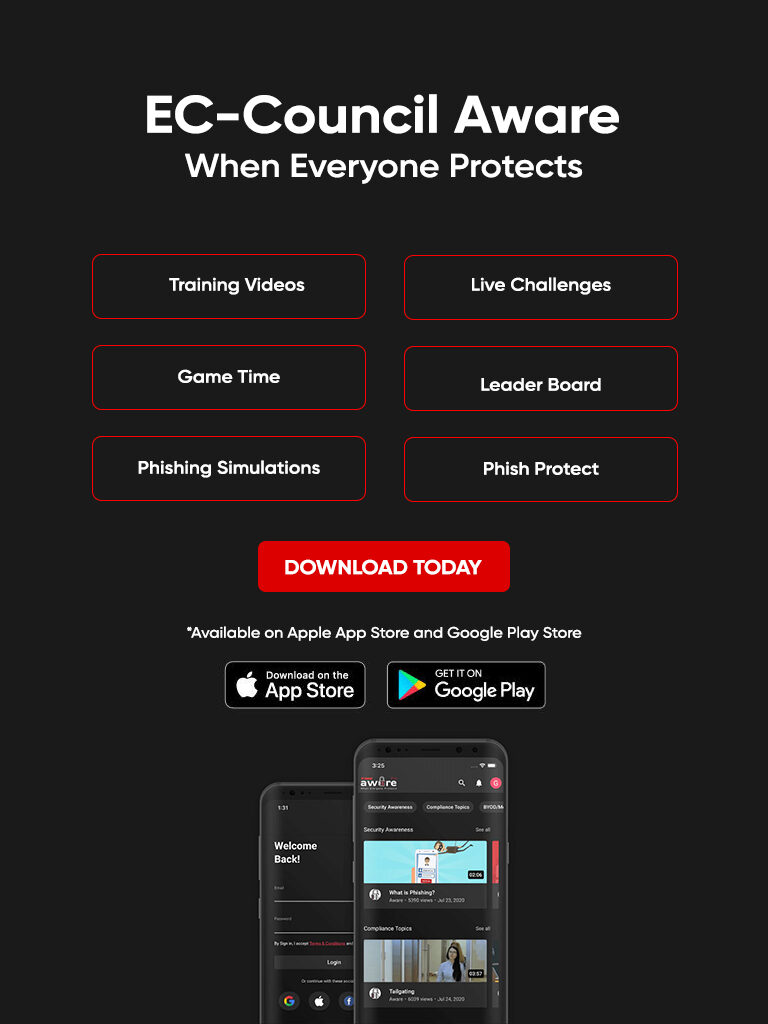
CONSULTING AND ADVISORY SERVICES
![]()
Checkout the virtual tour of EC-Council Cyber Defense, The Next Generation SOC, state of an art facility in Malaysia with all capabilities to serve clients globally.
![]()
CASE STUDIES
![]()
Power Manufacturing
Industrial Manufacturing
OUR TEAM MEMBERS ARE CERTIFIED
BY THE TOP CERTIFICATION BODIES
![]()