A majority of organizations are highly dependent on third-party vendors for services in order to save costs and raise the quality of service.
By relying on a third-party vendor, it also means that confidential data and information about an organization will be handled by a third party, which could lead to serious consequences.
In current organizations, various vendors are engaged to provide a variety of services; hence, it is imperative to have a sustainable and scalable vendor management framework that ensures best-in-class vendor management processes and vendor performance across various vendor services. Implementing a sustainable and scalable vendor management program ensures that all vendor-related risks are mitigated and vendor management processes are well defined as per industry-leading practices.
Our Approach:
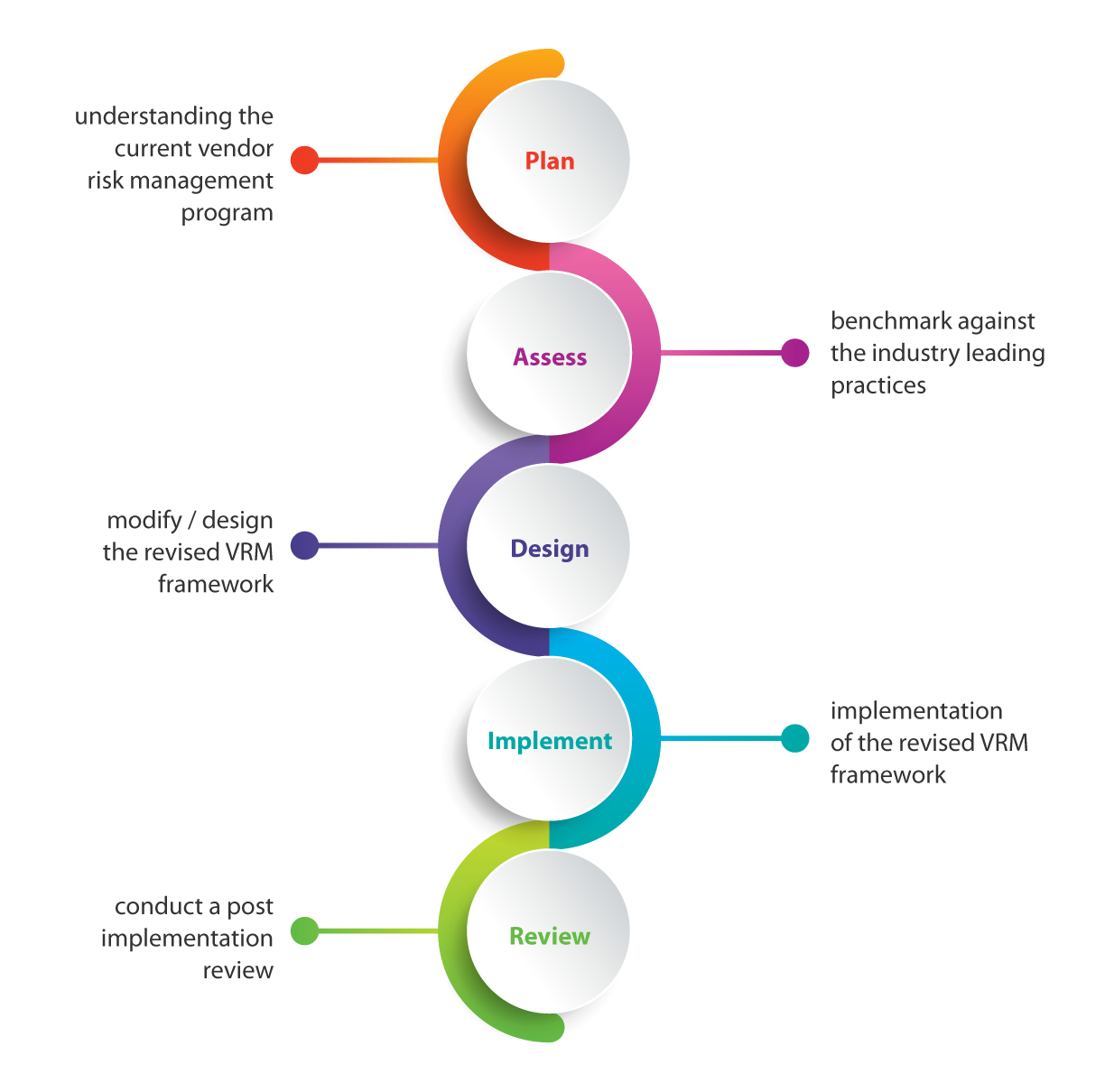
Putting a robust vendor management process in place will allow organizations to achieve the following benefits:
- Established robust vendor management processes to ensure effective services from the vendors and mitigate risks related to vendor services, vendor availability, contractual breach, and service quality.
- Clearly defined roles and responsibilities among vendor management stakeholders, which leads to effective decision-making.
- Well-defined SLA and performance-monitoring mechanisms to ensure compliance to agreed contractual terms.
- A well-defined risk management process to ensure proper risk profiling of the vendor and implementation of required risk mitigation.
- Adherence to audit and compliance requirements by following all defined processes as per the vendor management framework.
EGS shall perform:
- “As-Is” assessment and gap analysis against the existing framework.
- Policies & procedures including defining the scope of the framework inclusions.
- Roles & responsibilities, RACI matrix.
- SOPs for lifecycle management activities for existing vendors and onboarding of new vendors.
- Categorization criteria and categorized list of vendor repository based on criticality of vendor and access to 24*7 network/data.
- Prepare Vendor Assessment checklist.
- Compliance Metrics and reporting including the frequency of auditing, testing, and escalation mechanisms.
- Vendor Selection Process and criteria
- Vendor Assessment and Risk Management program including relevant checklists.
- Stakeholder awareness and involvement strategy.
We’re here to help!
Are you looking for more information? Or do you want to book a meeting?
Connect with an EGS Security Specialist

