Top Cybersecurity Services That
You Need to Stay Safe
- Vulnerability Assessment and Penetration Testing (VAPT)
- Remote Penetration Testing
- Business Continuity Planning and Disaster Recovery Strategy
- Cybersecurity Posture and Maturity Assessment
- Cloud Security Services
- Digital Forensics
- ISO 27001 Advisory
- Compromise Assessment
- Identity and Access Management Policy
- Security Operations Center (SOC)
According to Star Online, cybersecurity cases in Malaysia have reached 82.5% during the Movement Control Order (MCO) against the last year’s records. The study recorded 838 security incidents in less than a month from all across Malaysia, including Kuala Lumpur, Seberang Perai, George Town, Ipoh, Shah Alam, and Malacca. Under this elevated risk of cybercrimes, Malaysian enterprises need compromise assessment to determine if their network or devices are compromised.
The assessment seeks to find attackers currently in the environment or those active in the recent past. It measures the level of risk posed by them recommending actionable countermeasures.
The assessment seeks to find attackers currently in the environment or those active in the recent past. It measures the level of risk posed by them recommending actionable countermeasures.
Compromise assessment service is a comprehensive technical assessment and analysis of an organization’s infrastructure, endpoints and servers to look for indicators of compromise or any evidence of malicious activities.

WHY Is a Compromise Assessment Important?
Are your teams working from home due to the COVID-19 outbreak lockdown? Have you assessed if your networks and end-user devices can be compromised? In fact, are you sure your network or systems are not already compromised? If these are questions bothering you, NOW is the best time to act. EC-Council is offering a FREE Compromise Assessment of your teams while they work from home.
The survey detects and exposes ongoing and historical cyberattacks in security infrastructure. When it comes to having a cybersecurity policy, many organizations do what is recommended to meet compliance regulations. The remaining risk is either ignored or offloaded to an insurance policy. If your organization follows a similar approach, a regular compromise assessment should be incorporated into your risk mitigation strategy. This will ensure that your business environment is not compromised by attacks that your current resources do not detect.
Security Assessment Is NOT Compromise Assessment
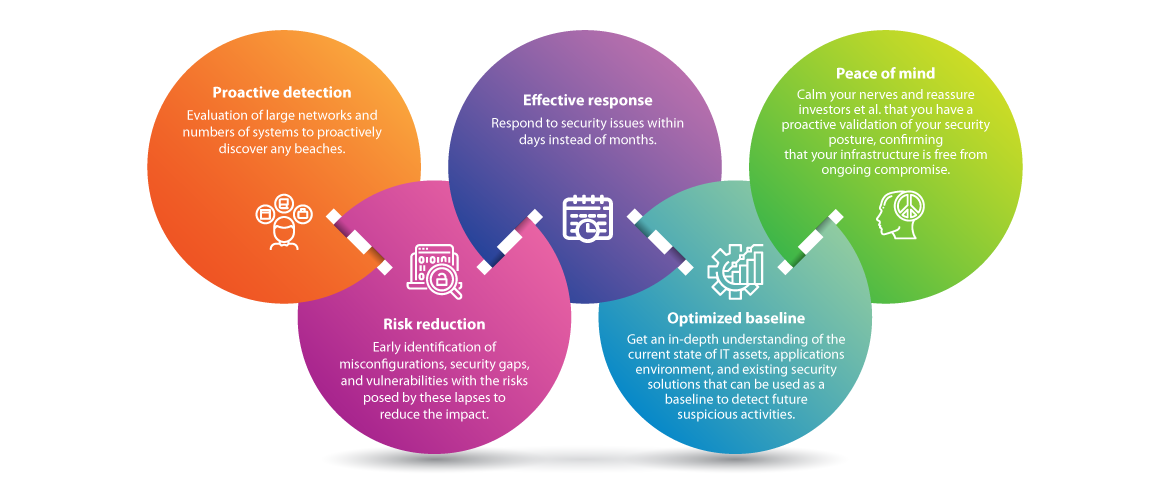
The main focus of security assessment, such as penetration testing, is identifying the weaknesses and vulnerabilities within your organization’s digital environment. What it does not tell you is whether you’ve been breached or not. On the other hand, compromise assessment is a proactive validation of your security posture that identifies known and zero-day attacks, confirming that your infrastructure is free from ongoing compromise.Key Benefits of Compromise Assessment
Why EGS?
| Mixed Protection EC-Council Global Services employs a well-established combination of automated tools and manual validations to ensure the Indicators of Compromise (IoC) are well monitored, identified, and validated. |
| Advanced Techniques: Our experts not only rely on IOCs but deploy advanced assessment techniques such as correlation-based anomaly detection, cooperative behavior analysis, and retrospective pattern recognition – all designed to identify the most sophisticated malicious activities. |
| Complimentary Services We have dedicated teams for incident response and digital forensics on standby to help you handle incidents, investigate further, and provide in-depth root cause analysis. |
How it works:
- Planning and scoping
- Sensor deployment
- Monitoring and data collection
- Artifact analysis
- Reporting
Deliverables:
- Complete list of vulnerabilities, if any
- List of misconfiguration and gaps, if any
- Full malicious/ suspicious activity report
- Recommendation on response and remediation
- Initial incident response/ digital forensics strategies
We’re here to help!
Are you looking for more information? Or do you want to book a meeting?
Connect with an EGS Security Specialist