What Does SOC Stand for? Who Needs SOC and Why?
An information Security Operations Centre is a computing facility dedicated to housing the information security team responsible for monitoring and analyzing cyber threats, 24×7. Cyber SOC is responsible for monitoring and analyzing cyber incidents to defend networks against sophisticated and evolving threats. Uniformly, a SOC team consists of experienced security analysts and engineers overseen by managers working cohesively alongside the incident response team to ensure early warnings are addressed.
In general, SOC benefits us in meeting standards, regulatory requirements, security monitoring, threat, and incident response management. Regardless of the sector or nature of the business, a SOC in any organization aims to defend security breaches and mitigate risks providing an upper hand in controlling and decision-making, which indirectly protects the company from contingencies like financial losses or reputation deterioration.

What Does a SOC Do?
A SOC consists of a team of experts providing analytical responses and suggestions to ensure critical security incidents are responded to, despite existing technologies that monitor endpoints, applications, IPS, or firewalls for cyber threats. Acquiring a competent team of SOC would benefit any business considering a skilled security team. Likewise, the qualified SOC team looks out for potential threats and passes them on for appropriate measures to be taken, which indirectly reduces the business downtime and ensuring business continuity.
In today’s environment, businesses cannot afford downtime. In the event of a breach, the SOC notifies the stakeholders on security incidents. A SOC is responsible for providing audit and compliance support to match government, corporate, and industry regulations requirements. The managed security services tools used by modern SOCs aggregates security data from across the organization to generate a detailed compliance audit and reports.
EC-Council Global Services – SOC Approach and Phases
EGS possesses a quintessential approach to provide the most effective assistance that fits our clients’ needs and comprehends their business and ultimate objective. For best results, EGS emphasizes on acquiring the best approach to aid business’ perquisites.
The Managed Monitoring Approach of EGS:
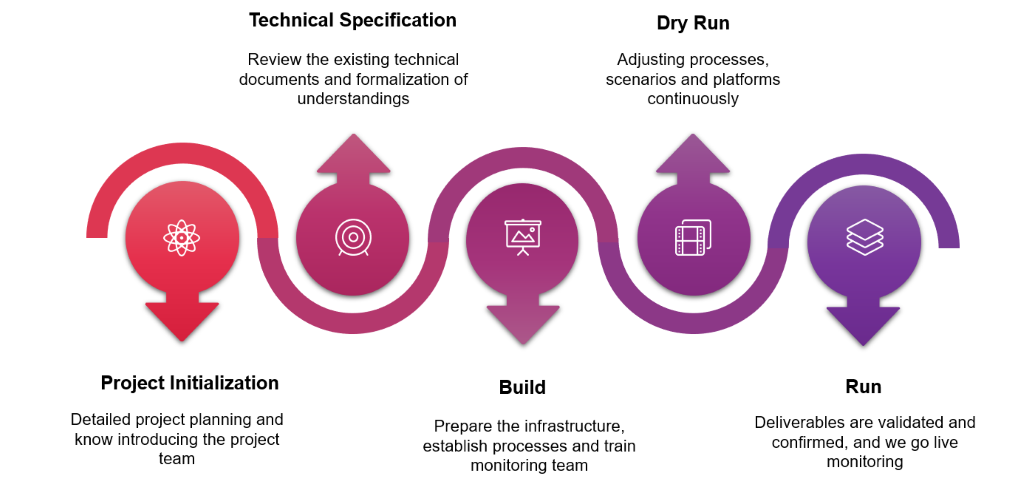
Phase 1
Project Initialization– Formalizing the start of a project with detailed planning on objectives, scope, deliverables, and timeline with the stakeholders.
Phase 2
Technical Specification – Involves data gathering of existing operational processes and procedures into a detailed document.
Phase 3
Build – Developing and implementing SIEM infrastructure suited for the client.
Phase 4
Dry Run– Conducting the pre-run of the monitoring process and verifying the solutions that meet the requirements established and generating sample reports.
Phase 5
Run – Upon validating deliverables, the project goes live, with round-the-clock monitoring and incident detection and periodic reports generation.
Why EC-Council Global Services SOC?
EC-Council Global Services SOC is positioned as an experienced and ISO 27001 Certified, for more than 20 years as a managed services provider. EC-Council Global Services SOC is geared to take the lead in providing IT managed services, particularly concerning cybersecurity. EC-Council Global Services SOC delivers around-the-clock managed comprehensive IT security needs, including a variety of consulting services.
EGS has been providing managed services to financial institutions and government agencies for nearly two decades. Our SOC team consists of professionals who are Certified Ethical Hacker (CEH), Certified SOC Analyst (CSA), and Certified Threat Intelligence Analyst (CTIA) having 15 years of experience. We strive to provide the best security services to our clients based on our vast experience in information security projects, and value-added services are part of our commitment to exceeding client’s expectations.

EC-Council Global Services SOC Service for Organizations
The key highlight of organizations’ benefitting from the SOC team is the three-tier approach, which involves detecting, reacting, and predicting. Potential threats or vulnerabilities are identified through continuous monitoring and analysis across the organization’s networks, servers, and endpoints (24×7). The security incident is responded promptly with the correlation workflow and response network consisting of Level 1 and Level 2 security analysts. Subsequently, a managed security incident response involves the threat intelligence team.
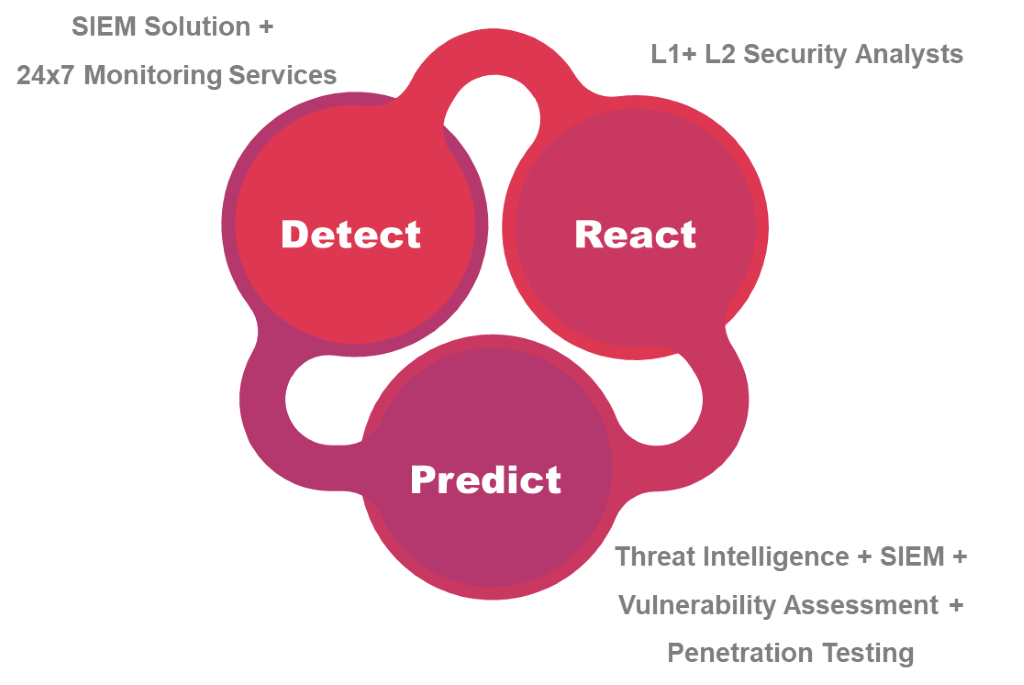
We support businesses by providing tailored use cases for the analysis of enterprise networks distinguishing the threats. SOC operates by managing known threats. Likewise, they operate to meet the organization’s nature of business and requirements corresponding to the potential threats or work within their risk tolerance. A successful SOC constantly embeds newer threat intelligence feeds into the monitoring tools to aid evolving cyber threats and to develop advanced use cases based on the feeds.
How EGS Can Help Your Business
Monitoring network security, availability, and reliability of a distributed environment, with the risk of exposure to potential threats, is one of the most significant concerns to any organization. As a result, organizations rely on IT security professionals’ assistance to administrate and effectively monitor the complex IT infrastructure. EGS is a leading global security and compliance management solutions provider, protects businesses by monitoring, determining, and alleviating internal and external cyber threats or risks across the organization to ensure the security of assets and processes from cyber espionage.
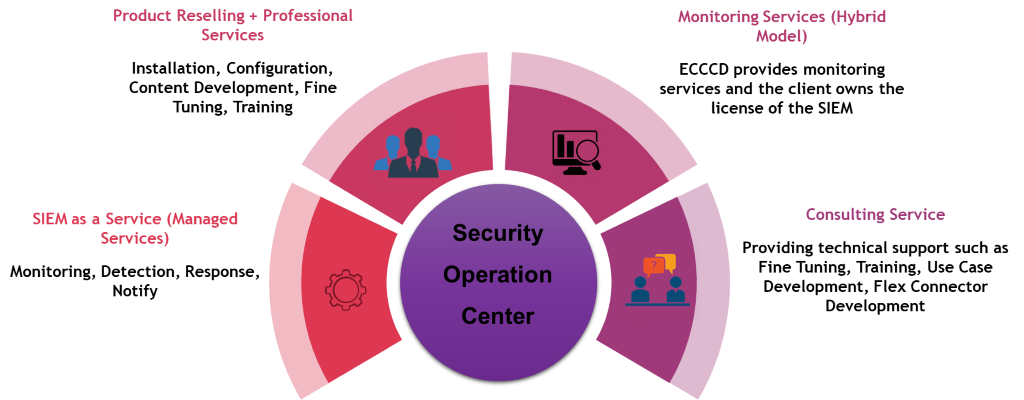
As on the list of EGS SOC services, we offer consulting services and adequate technical support for businesses seeking solutions based on the business risks.
We’re here to help!
Are you looking for more information? Or do you want to book a meeting?
Connect with an EGS Security Specialist

