Top Cybersecurity Services
You Need to Stay Safe
- Vulnerability assessment and penetration testing (VAPT)
- Remote Penetration Testing
- Business Continuity Planning and Disaster Recovery Strategy
- Cybersecurity Posture and Maturity Assessment
- Cloud Security Services
- Digital Forensics
- ISO 27001 Advisory
- Compromise Assessment
- Identity and Access Management Policy
- Security Operations Center (SOC)
Information Security Risk Management Advisory
Identify and achieve effective IT security management
Business growth and risks come hand in hand. Therefore, reducing the impact of these risks is a consideration that organizations cannot afford to overlook. Risk management is vital to any business, especially growing businesses.
As technology and infrastructure expand to cater to business growth, having a skilled team of consultants who can identify risks associated with information technology is critical.
Risk management not only allows you to review all the possible threats and risks to your organization, it also enables you to focus your security efforts and prioritize them on critical systems.
Key Risk Management Strategies Include
Why Is It Required?
A mature Information Risk Security Management System Framework is driven through a risk-based approach. It is imperative for organizations to be aware of the Information Security Risks that they are exposed to so that they can adopt appropriate strategies to manage them proactively.
To ensure that the security of sensitive data is protected, having a team of experienced and skilled consultants can help you evaluate the areas of weakness, loopholes in the system, and the necessary steps that should be taken by an organization to safeguard themselves, as well as to adhere to legal and regulatory compliances.


Who Needs It?
- All organizations that process, store, and transmit data, and have a dependency on technology.
- Organizations that want to identify, assess and mitigate risks, as well as ensure the confidentiality, integrity, and availability (CIA) of their assets
- Organizations that want to establish robust risk management processes to secure their critical business systems against cyberthreats
- Organizations that are required to comply with legal, regulatory and local requirements
EC-Council Global Services Methodology
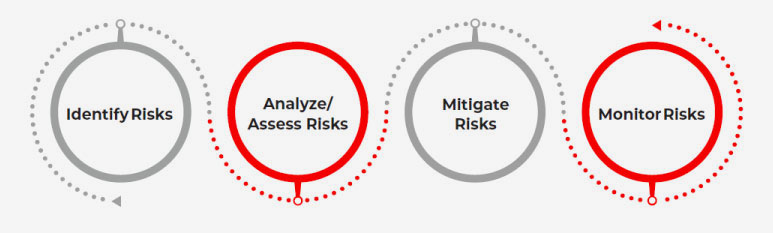

Why Should You Opt for a Information Security Risk Management Advisory?
- You can address significant risks that may impact your organization’s processes and procedures
- You can help avoid non-compliance to legal and regulatory requirements, as well as reputational damages and financial penalties that may stem from data breaches
- You can be confident that you have risk responses that are not only effective but adequate
Benefits
 |
We have a team of professionally trained, certified and highly experienced cybersecurity consultants who have previously assisted our clients in achieving a robust, flexible and scalable risk management |
| We can help you gain context and full control of the risks that exist within your organization |
| We can help you minimize the risk of data breaches |
| We can help you adhere to audit and compliance requirements by following all defined processes |
| We can protect all the efforts your organization has made in building your brand and maintaining the goodwill of your customers |
 |
We combine the best practices and standards (along with our methodology used globally) to identify, assess, evaluate, and manage the risks. |

