In a constantly changing information technology environment and with the rapid adoption of business models (such as SaaS, PaaS, Cloud, BYOD, etc.), major security challenges in an organization about whether the right users have access to intellectual property, networks, or resources of a company have emerged. EGS provides an identity and access management service to ensure that the right personnel gets the right resources the right way and for the right reason.
EGS Approach:
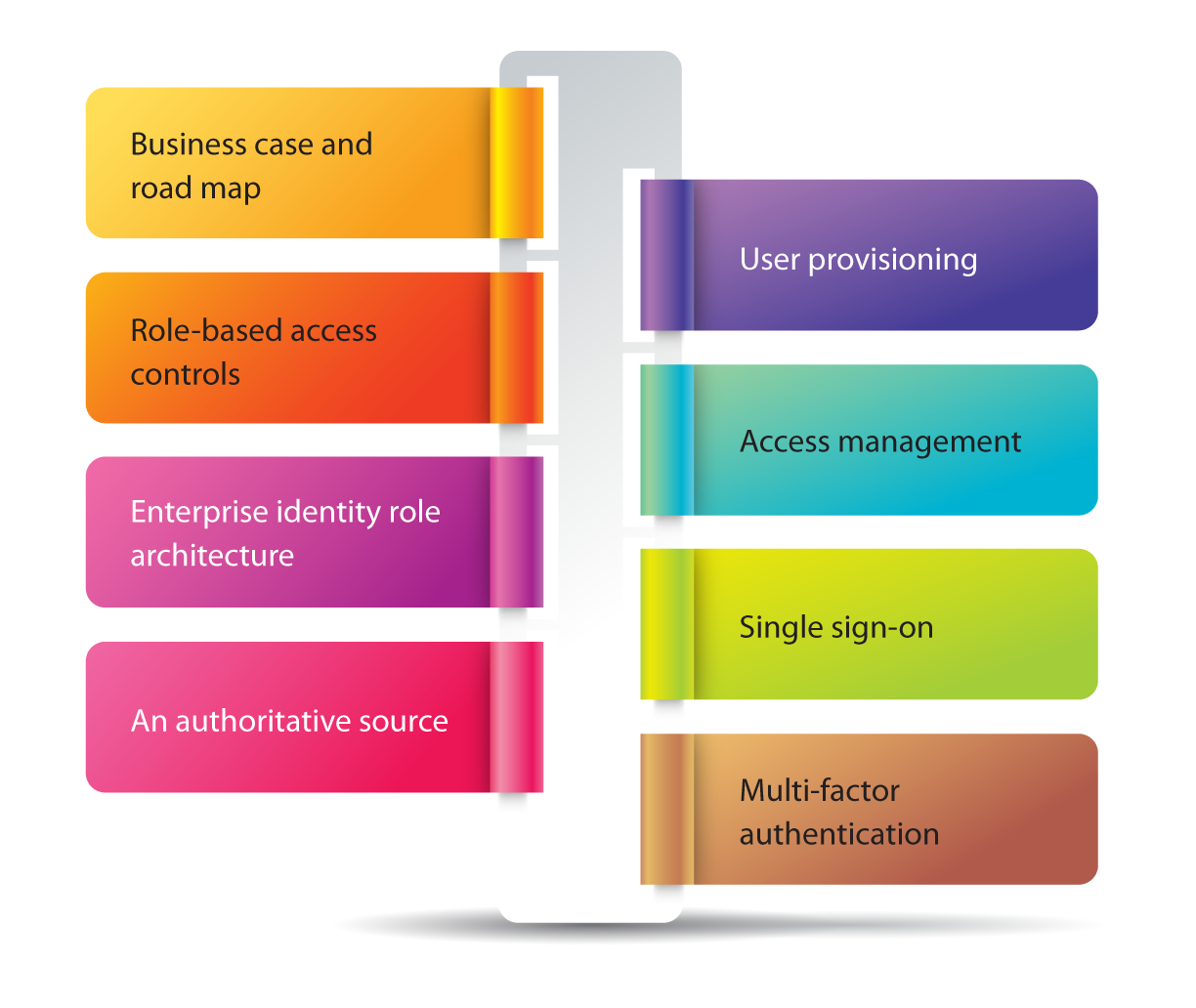
Why do we need Identity Access Management?
Enterprise IT infrastructure has become relatively commonplace as the role of IT systems has become increasingly important. Moreover, when an organization implements a bring-your-own device (BYOD) policy in the workplace, each of the employees may have more than one device; this makes managing the services and devices more difficult for administrators. An effective identity and access management system can help the organization to manage all devices, as well as mitigate security risks posed to an organization and assure that the organization stays compliant.We’re here to help!
Are you looking for more information? Or do you want to book a meeting?
Connect with an EGS Security Specialist

