Why read this report
Client, a leading investment company deals with security services, electronic security monitoring, and detection systems, e-commerce consulting, and product development services through its subsidiaries.
Apprehensive about rising cyber threats, the organization was looking to secure and protect their IT infrastructure against external vulnerabilities and threats. All this, while ensuring that they were compliant with the industry’s best practices and guidelines.
This report presents an assessment to ensure that cybersecurity controls are applied throughout the enterprise. It aims to improvise and fortify the organization’s IT security from emerging cyber threats. It also helps anticipate key cybersecurity developments and provides appropriate solutions to help reduce risks. This is done while making compliance an integral part of the strategy.
Key takeaways:
- Identify threats and risks posed within the e-commerce system while considering the use of automatic tools.
- Evaluate if the systems were susceptible to any known risks or threats, assign severity levels to those risks or threats, and recommend mitigation.
- Ensure compliance with the latest industry standards and mandates.
CASE STUDY
SECURING ON THE NEXT LEVEL IN CYBERSECURITY
A financial institution goes beyond compliance to ensure customer trust.
Situation
The Financial industry is one of the most targeted sectors by cyberattackers. Concerned about the rising threats in cybersecurity, client, a financial company, is looking to establish a robust security operation to protect their financial and paramount customer information. All this, while ensuring that they are compliant with the industry’s best practices and guidelines.
To establish security standards with complaint controls and defensive strategies, client approached EC-Council Global Services. The challenge was to understand the huge source code, which is in the combination of multiple code languages, and then identify existing vulnerabilities.
Solution
EGS engaged a team of experts to test the security controls, defenses, and designs of the application from the outside-in, with little know-how of their applications, internal workings simulating a real environment of security threat.
During this time, the EGS team –
- Defined, identified, classified, and prioritized the vulnerabilities and threats posed by their e-commerce system considering the usage of automatic tools.
- Tested their security controls and updated the management regularly on critical findings based on the Common Vulnerability Scoring System (CVSS).
- Provided a vulnerability report assuming that the client is aware of the severity of threats.
These were assessed and validated using industrial practices and guidelines such as CIS, DISA STIG, and NIST to identify any non-compliances.
CIS (Center for Internet Security) – CIS Benchmarks are best practices for the secure configuration of a target system. CIS Benchmarks are developed through a unique consensus-based process comprised of cybersecurity professionals and subject matter experts around the world. CIS Benchmarks are the only consensus-based, best-practice security configuration guides both developed and accepted by the government, business, industry, and academia. Proven guidelines will enable you to safeguard operating systems, software, and networks that are most vulnerable to cyber-attacks. They are continuously verified by a volunteer IT community to combat evolving cybersecurity challenges.
DISA (Defense Information Systems Agency) – The DISA serves U.S soldiers globally, allowing them to access crucial information worldwide through services like computer hosting, information assurance, multinational information sharing, and data services. DISA’s information systems are used across the full spectrum of military force operations, including offensive tactics, defensive tactics, counterterrorism, and humanitarian efforts.
STIG (Security Technical Implementation Guide) – A Security Technical Implementation Guide (STIG) is a cybersecurity methodology for standardizing security protocols within networks, servers, computers, and logical designs to enhance overall security.
NIST (National Institute of Standards and Technology) – NIST implements practical cybersecurity and privacy through outreach and effective application of standards and best practices necessary for the U.S. to adopt cybersecurity capabilities. NIST’s cybersecurity programs seek to enable greater development and application of practical, innovative security technologies and methodologies that enhance the country’s ability to address current and future computer and information security challenges
Services delivered
EGS offered a comprehensive range of services:
| External Vulnerability Assessment (Blackbox) |
| External Web Application Assessment (Blackbox) |
| External Web Application Assessment (Grey box) |
| Internal Vulnerability Assessment (Whitebox) |
| Internal Penetration Testing (Grey box) |
| Internal Web Application Assessment (Grey box) |
| Thick Client Application Assessment (Grey box) |
| Host Configuration Review |
| Database Configuration Assessment |
| Data Center Physical Security Assessment |
| Network Architecture Review |
| Wireless Assessment |
| Cloud Security Configuration Review |
Recommendation
Post assessment, a report, including recommendations, was provided to the client to close any loopholes in the existing cybersecurity strategy. These recommendations were divided into two groups: tactical recommendations for immediate improvement and long-term strategic recommendations for improvement.
- The report gave the client a clear and realistic view of its cybersecurity position and an actionable plan to improve it.
- The report laid the foundation for a lasting security culture and anchored in the core values and strategy of the organization.
The following diagrams provide a summary of findings and remediation status:
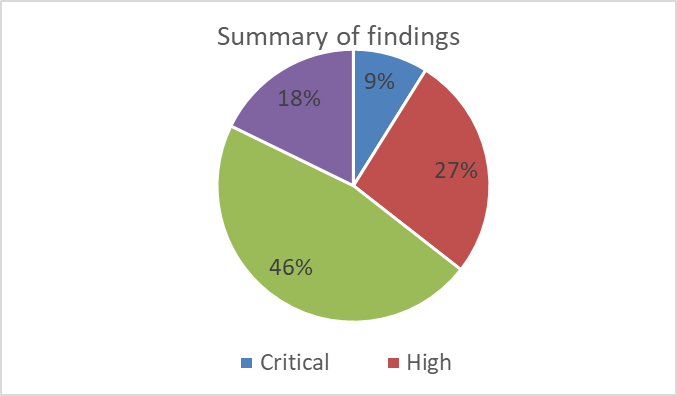
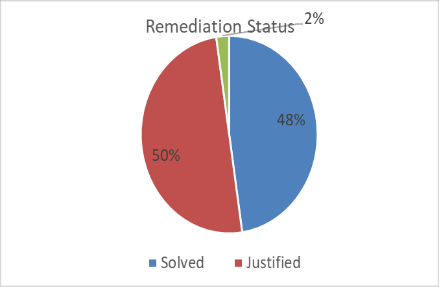
Results
The solutions gave the client an analysis of the gaps and misconfigurations in their existing IT systems, as well as a list of shortcomings when aligning the current cybersecurity strategy with the industry’s best practices and standards. All these findings were categorized into low, medium, high, and critical severity ratings and the client was provided with comprehensive remediation procedures.
Engage with EGS: Gain greater confidence in your cybersecurity decisions by working with EC-Council Global Services’ thought leaders to apply our solutions to your specific business and technology initiatives.
| Posture Assessment Survey
An independent expert assessment of the current state of information security environment is conducted against global standards and leading industry practices to measure the overall cybersecurity maturity of your organization. |
FREE Phishing Simulation
To assess your organization’s human error vulnerabilities, take OhPhish’s FREE subscription to run simulated Phishing attacks and get a detailed actionable report. |
Vulnerability Assessment & Penetration Testing (VAPT)
EGS offers a broad range of network infrastructure, web applications, and mobile application security assessment services designed to detect and gauge security vulnerabilities. Take the FREE VAPT for up to 10 external IPs, worth USD 5000 and get a customized report! |
Related Research Documents/Links
https://blog.eccouncil.org/10-proven-statistics-about-cybersecurity-in-financial-institutions/
https://www.youtube.com/watch?v=ftO_GUwMm5w
https://youtu.be/Nnf2dZ_ccS4
https://blog.eccouncil.org/purpose-of-intelligence-led-penetration-and-its-phases-1/
https://blog.eccouncil.org/purpose-of-intelligence-led-penetration-and-its-phases-2/
https://blog.eccouncil.org/purpose-of-intelligence-led-penetration-and-its-phases-3/
https://blog.eccouncil.org/purpose-of%e2%80%afintelligence-led-penetration%e2%80%afand-its-phases-4%e2%80%af/
