Top Cybersecurity Services That
You Need to Stay Safe
- Vulnerability assessment and penetration testing (VAPT)
- Remote Penetration Testing
- Business Continuity Planning and Disaster Recovery Strategy
- Cybersecurity Posture and Maturity Assessment
- Cloud Security Services
- Digital Forensics
- ISO 27001 Advisory
- Compromise Assessment
- Identity and Access Management Policy
- Security Operations Center (SOC)
Secure Your WFH Teams With
Remote Penetration Testing
Is your distributed network secure enough to withstand a cyberattack? Have you tested your security strategy for WFH teams to ensure that you are doing things right? With remote penetrating testing services, you can strengthen your security strategy by exposing all existing vulnerabilities and finding ways to fix them.
With cyberattacks only increasing as the days pass, knowing your vulnerabilities and how attackers could exploit them is one of the best insights you can get to help you improve your cybersecurity. EC-Council Global Services can help you simulate a real-life cyber-attack to assess if your existing cybersecurity strategy is strong enough to weather the storm.
What is Penetration Testing?
A penetration test helps determine whether an IT system is vulnerable to a cyberattack, whether the defensive measures are sufficient, and which security measure failed the test. It shows the strengths and weaknesses of any IT infrastructure at a given point in time. The process of a penetration test is not casual; it involves a lot of planning, taking explicit permission from the management, and then initiating tests safely without obstructing regular workflow.Why Do We Need Penetration Testing?
It is important to have skilled professionals who can defend the security system against cybercrimes to ensure a healthy and secure environment in an organization. Some of the reasons why organizations need penetration testing are:
01 – Uncover vulnerabilities before cybercriminals exploit them
02 – Reduce network downtime
03 – Initiate a highly efficient security measure
04 – Enable regulatory compliance
05 – Protect the company’s reputation and customer trust
What Are The Different Types of
Penetration Testing?
There are three types of penetration testing
| Black Box Penetration Testing: A penetration tester has no previous knowledge of the targeted system. |
| White Box Penetration Testing: A penetration tester has complete knowledge of the system to be tested. |
| Gray Box Penetration Testing: A penetration tester has limited knowledge of the system to be scanned. |
How is Penetration Testing Done?
There are many techniques used to conduct a penetration test. When it comes to EC-Council Global Services, here is the methodology that we follow:
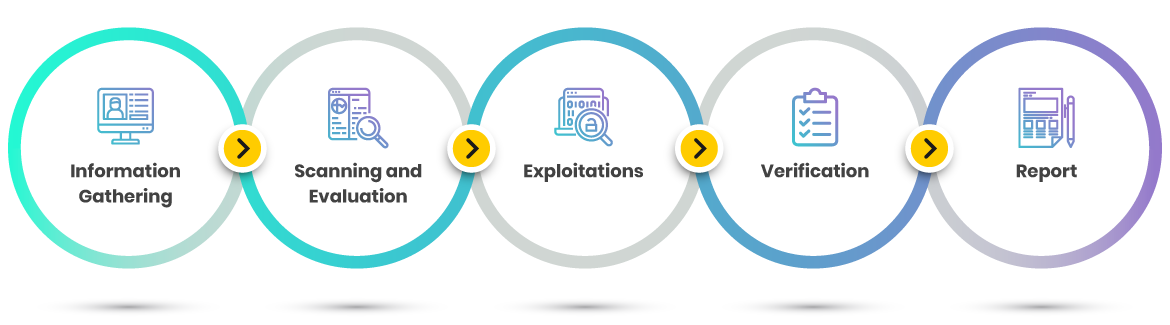
The EGS Methodology
- Information Gathering: Collect as much information as possible to gain a better understanding of the test environment.
- Scanning and Evaluation: Perform an automated scan on the target along with manual verification of findings.
- Exploitations: Exploit the vulnerabilities identified from the scanning phase through the use of both automated and manual techniques
- Verification: Conduct manual verification and analysis to validate all the findings based on test cases and standards.
- Report: Document all verified findings with their severity rating base on best practices and standard rating scores.
What Areas Are Tested?
Look at the following to ensure that you are getting the most
from your penetration testing vendor:
Areas Most Tested
Infrastructure |
WEB Application |
Mobile Application |
|
|
|
What should be included in a penetration test?
Every penetration test must include a report which not only explains the details of how the test was conducted but also shows the various vulnerabilities found and solutions to improve your security.
EGS Severity Rating System
EGS Severity Ranking is mapped with industry proven rating systems such as OWASP risk rating and CVSS version 3.
Critical
A vulnerability that can be exploited without user interaction and likely allows attackers to take complete control of applications (web/mobile/client-servers), servers, or databases. Attackers can gain elevated privileges without any specific conditions and may be able to escalate attacks to other systems and applications via lateral movement
High
Vulnerability exploitation allows attackers to gain access to applications or systems without specialized access and complexity. Attackers can acquire sensitive information that can significantly compromise the confidentiality, integrity, or availability and can be used to escalate access privilege or to find other vulnerabilities and exploits.
Medium
Successful exploitation may require user interaction or specific conditions and circumstances. A target application/system can be compromised partially, which provides attackers with limited access.
Low
A vulnerability that is not exploitable and has a minimal impact on applications, systems, servers, and databases. These vulnerabilities are generally not exploitable and most likely be used in conjunction with other vulnerabilities and to escalate an attack.
Information
Publicly available information that is not supposed to be visible to end-users. It does not have any direct security impact on targets; however, it may help attackers to narrow down their attack scope.
What are the best penetration testing tools?
Some of the most popular penetration testing tools are- NMap (or the Network Mapper)
- Metasploit
- Nessus Vulnerability Scanner
- Wireshark
Testing Tools That We Use
Below are several industry-proven tools that we use to carry out a vulnerability assessment. Additional tools may be used depending on the case.- Nmap
- Nessus
- Acunetix
- Metasploit
- Burp Suite
- OWASP ZAP
- Wireshark
- Exploit kit
- APKtool
- Drozer
- Mobsf
How often should a penetration test be done?
Cybersecurity Ventures suggests that cyberattacks are the fastest growing crime and will cost the world $6 trillion a year by 2021.A penetration test is not a one-time activity. As technology advances, so do cybercriminals. As networks or computer systems are exposed to vulnerabilities, there is a consistent change in their performance. How often a company should penetration test depends on factors such as:
- The size of the company
- Compliance with various regulatory laws
- The existing infrastructure
How much does a penetration test cost?
As with any cybersecurity service, the cost of a penetration test differs based on the following set of variables:- The size and complexity of your network devices and environment.
- The methodology used as the different methodologies call for a different set of tools and varied techniques.
- The type of experience the penetration testing vendor brings to the table. What type of skillset do they possess? Are they certified and experienced professionals?
- If it is a remote penetration test, or will it be conducted onsite?
- The details in the report and solutions
Get your remote Penetration Testing done by
EC-Council Global Service (EGS)
Indeed, EC-Council Global Services provides clients with top-notch remote penetration testing services to identify known and unknown (zero-day) vulnerabilities, weaknesses, and gaps. Markedly, EGS analyzes the findings and associated risks followed by the comprehensive report, including a recommendation on remediation.
EGS adopts industry-proven technologies and standards such as OWASP, CREST, and OSSTMM. In addition, EGS combines robust manual penetration testing and finding validation conducted by highly skilled and certified professionals. In due time, EGS ensures the highest level of quality regardless of the geographical position of clients.
Highlights of Remote Penetration Testing with EGS
- High availability: Due to remote penetration testing, EGS can offer its services to any clients globally from different regions regardless of distance or any particular situation such as regional or global crisis.
- Geographic diversity: While the EGS penetration testing team consists of several certified cybersecurity professionals from all around the world. Correspondingly, with remote penetration testing, a client can easily engage EGS teams beyond geographic barriers.
- Fast and flexible: Remote penetration testing offers higher speed, and better flexibility as this type of testing only requires an IP range, URL, or remote access.
Our People, Our Strength
- Our penetration testing team is made of highly skilled and certified professionals with a proven record of delivering complex projects on a global scale.
- Our R&D team continuously reviews the approaches and methodologies of penetration testing. Forthwith, to ensure they align with industry-proven standards and frameworks such as OWASP, CREST, and OSSTMM.
- We employ comprehensive manual verification in addition to the use of automated tools. Consequently, ensures a high level of accuracy in the reports.
- We provide a cost-effective engagement that fits perfectly into your budget.
- Nevertheless, we produce a detailed and precise report with a meaningful summary, crafted for C-level executives, of the engagement.
We’re here to help!
Are you looking for more information? Or do you want to book a meeting?
Connect with an EGS Security Specialist

