
Credential stuffing is the new and trending method of cyber attack wherein the attacker inserts lists of hundreds of millions of breached usernames and passwords into a system. As its physically impossible for a single person or group of people to manually enter each username-password combination into the system, automation tools such as Selenium, cURL, PhantomJS, or tools specially designed to effectively carry out automated credential stuffing attacks on the hacker’s behalf like Sentry MBA, SNIPR, STORM, Blackbullet, Openbullet, etc., are used. Also, as many websites today use captcha or advanced antibot technologies to defeat bot attacks, hackers have also developed credentials stuffing technology with captcha bypassing tools such as Anticaptcha, Buster, Rumola, ReCaptcha Solver, etc.
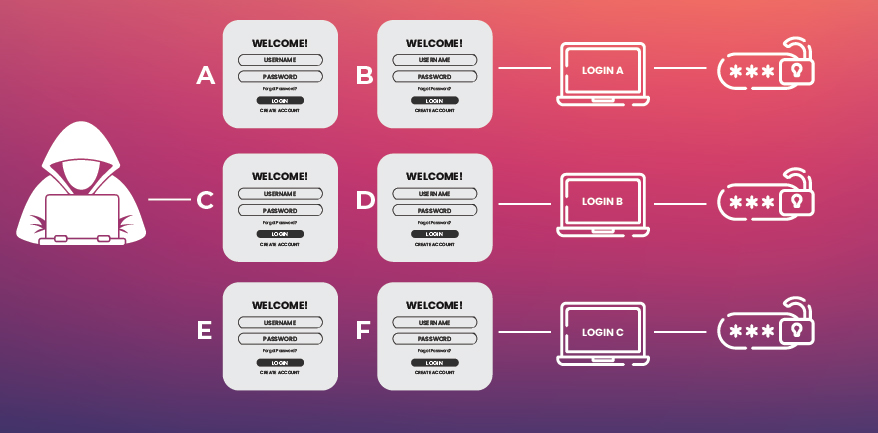
This attack uses automation tools to try a single time login attempt with the stolen/breached username and password data, as multiple attempts will raise a red flag with the security engineers, thus, increasing the risk for either the attackers them or their process to be exposed. The theoretical approach to this attack can be described as:
- Procurement of breach and compromised data from the dark web or other malicious platforms
- Sorting the data according to its corresponding login page or website
- Using automation tools to access the page, insert the credentials, doge/bypass the captcha, and test the success of login
- Frequently and periodically jump/change IP address, browser and other elements that may alert the IDS (Intrusion Detection System)
- Record the successful candidates and save them.
- Working on the successful credentials to further any malicious attempt
The successful stuffing is typically followed by financial gains as this attack is mostly done on online banking accounts or on other accounts and portals such as emails, social media, payment portals (API’s), online shopping websites, etc., that contain any financially exploitable information. Unlike credential cracking, which uses brute force and dictionary attacks to guess the password, credential stuffing uses compromised username and passwords (mostly the end products of a breach or information theft) paired with the automation process to simply automate the logins for millions of credential pairs from the list using standard web automation tools.
Penetration Testing
Penetration testing or ethical hacking is the authorized simulated cyberattack on a system/network to review and evaluate the targets’ cybersecurity posture, i.e., to identify the strength and weaknesses of an organization’s cyber landscape. This is usually carried out by licensed pen tester on the request of the organization that intends to test its network for vulnerabilities. This process is attempted just as how an actual malicious hacker (black hat hacker) would intend to carry out an attack, i.e., via the standard kill chain methodology but in a controlled and authorized environment. Thus, earning these pen testers the name of white hat hackers or ethical hackers. The process typically identifies the vulnerabilities in a system/network and tries to exploit those vulnerabilities in order to test the comprehensive defense postures and to project the magnitude of any probable attack. The time required for penetration testing differs with respect to the amount of target data shared with auditors. A penetration test aims to help organizations determine the system’s ability to withstand an attack and to discover any potential vulnerabilities. The current article discusses credential stuffing in-depth and how a penetration tester or ethical hacker could use it to test an organization’s web application security.
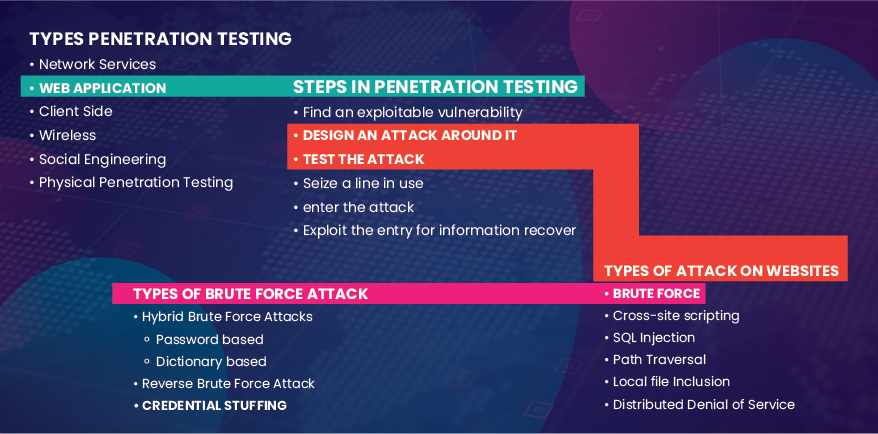
Figure: Classification of credential stuffing in the lattice of penetration testing
How Does Credential Stuffing Work?
As described earlier, credential stuffing extensively relies on automation; hackers do not literally type millions of credential pairs into the login boxes across thousands of sites manually. Also, the process cannot be attempted for all the records from a single IP address nor are multiple tries allowed for a single IP as many websites have rate limiting and antispam/antibot protections in place to block flooding of requests. Many credential stuffing tools are available on the dark web and other malicious platforms, such as:
- Incorporation of proxy lists and VPN to change the IP address frequently during the process
- Manipulating login properties and cookies to look as if the requests are being made from different browsers
- Integrating with different platforms built to doge or defeat the captcha program
Let’s demonstrate a small part of automation testing using a website meant for such web scraping & testing purposes (testing-ground.scraping.pro) and Python 3.8 programming language. As the modules required for this programming are Selenium and web driver for the corresponding browser; the example below uses the Chrome browser. The coding is explained step by step as follows:
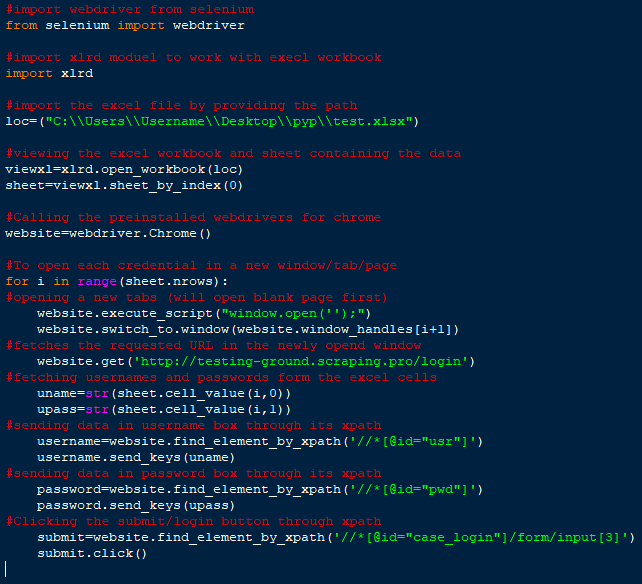
- Installing modules: Before importing selenium and chrome driver, they need to be downloaded and installed through pip command ‘pip install selenium’ for Selenium and the web driver as instructed by the corresponding browser properties. For Chrome, the web driver can be downloaded from ‘https://chromedriver.chromium.org/downloads’ and installed; the path of chrome drive needs to be specified in the system environment variables as shown below. For Windows 10: Control Panel\System and Security\System ⟶ Advanced system settings ⟶ Environment Variables ⟶ Path ⟶ New ⟶ add the path of Cehrome driver

- Importing webdriver: The first step in the code construction is importing webdriver through Selenium (a portable module to test web applications) as it will be used to open Chrome windows to demonstrate the automation process
- Importing xlrd: Many modules exist in Python to import excel for various purpose such as xlwt, OpenPyXL, XlsxWrite, etc, This example uses xlrd as the purpose here is only to read the data from Excel
- Obtaining the file through providing its location to a variable loc
- Opening the excel file from the given location and assigning it to a variable viewxl with the help of command open_workbook (loc)
- Calling webdriver for Chrome and assigning it to a variable website
- As each username, password pair needs to be displayed in a different tab, for loop is used to perform the following actions repeatedly:
- For each row in Excel, representing one username-password pair, a new tab/window is opened using exicute_scritp (“window.open(‘’);”) to open a Chrome window and website.switch_to.window (website.window_handles [i+1]) to open new tabs up till i+1; where i is the row number in excel currently being executed. As for loop starts with the count of zero thus, ending before reaching the actual length of list one is added to the value of i to reach that length
- Get (‘requested URL’) fetches the desired URL in each tab
- The cells in Excel are addressed as a combination of (row, column) number and are fetched with the help of cell_value (i,0/1) where 0 and 1 are the first and second columns respectively. The contents of the cells are converted to strings and assigned to variables uname and upass respectively and are done so the earlier command returns only float values for numbers. Thus, if any username or password value is a number e.g. “123” will then be returned as “123.0”, a float
- The xpath of the username and password entry boxes are collected through the target website’s element panel and assigned to variables with the help of find_element_by_xpath (“xpath value”)
- Username and password data is sent to those xpaths though send_keys (uname) function
- The submit button is clicked by using its xpath as above and using click() function
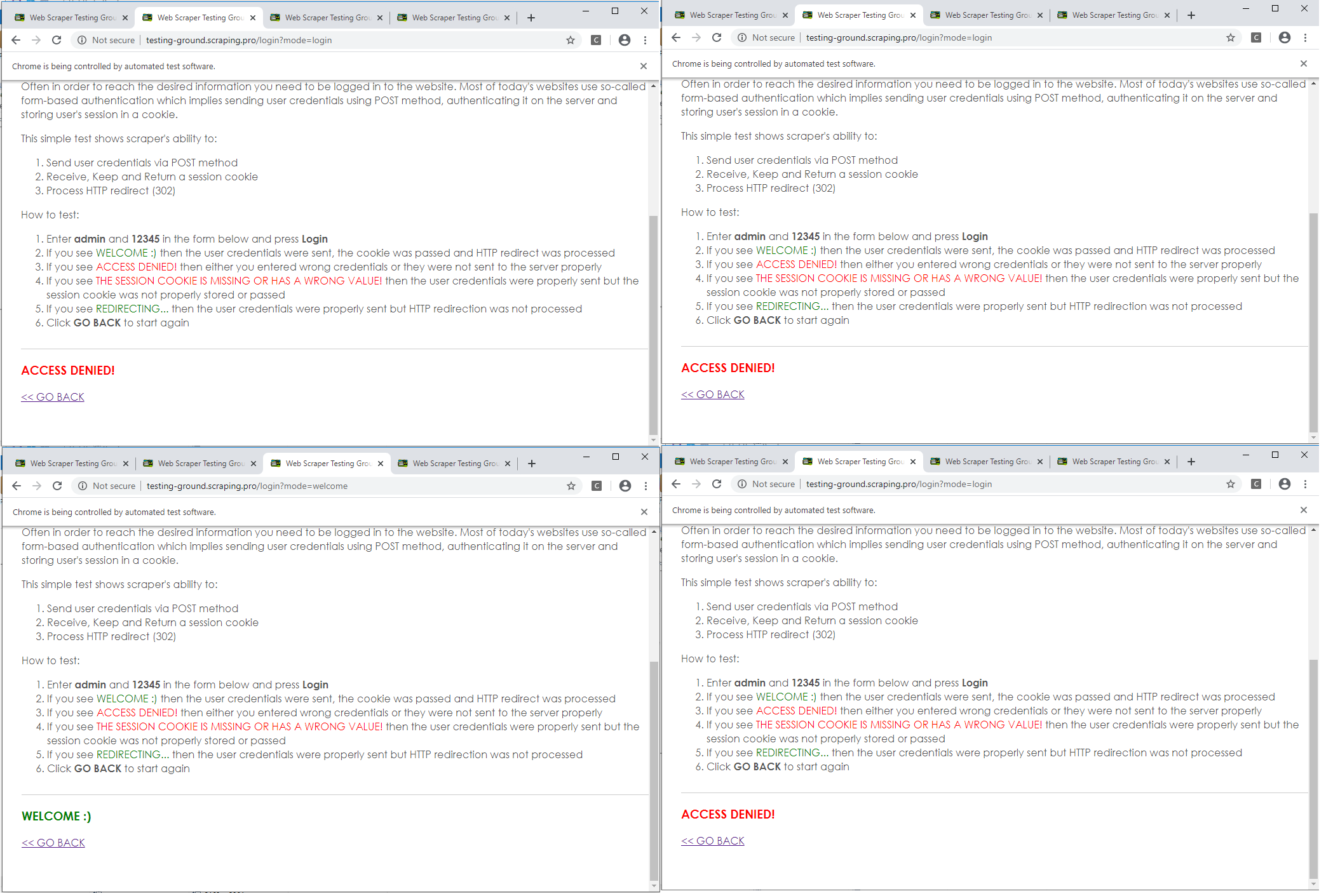
The result of the coding could be displayed as in the figure after running the code. The Time module could be imported and time.sleep () function could be used to see the workings of the program in slow motion. As seen from the images of random samples, access was denied for invalid credentials and a “welcome” sign was displayed for the valid one, indicating a successful login.
Selenium is an open-source, portable and multivariant web-testing application that provides both domain-specific i.e. incorporation of Selenium with different programming languages such as C#, Groovy, Java, Perl, PHP, Python, Ruby and Scala, the resultant test of which can run against any browser, and a playback tool that lets users test their functions on its IDE platform, without the need of any programming language. The IDE of Selenium could also be implemented as extensions or addons with Chrome and Firefox. Selenium WebDriver accepts commands from the Selenese i.e. the augmenting programming language, or via a Client API (Application Programming Interface) and relays them to the browser. This process is implemented through a browser-specific driver (such as Chromedrive for Chrome browser), that sends commands to browsers (such as Firefox, Google Chrome, Internet Explorer, Safari, or Microsoft Edge) through launching them and retrieving the results.
Apart from Selenium, many different web automation tools can be used solo or in augmentation to programming languages such as
- Phantom JS: An open-source software that provides a JavaScript API for automated navigation, screenshot, user behavior, and assertions, and is used to run web-based application testing.
- cURL: Also pronounced as ‘curl’, this project provides a library and command-line tool to conduct network transfer protocols. libcurl supports cookies, DICT, FTP, FTPS, Gopher, HTTP/1[10] (with HTTP/2 support), HTTP POST, HTTP PUT, HTTP proxy tunneling, HTTPS, IMAP, Kerberos, LDAP, POP3, RTSP, SCP, SMTP, and SMB.
- Apart from tools there also exist suites and online platforms such as open bullet, which is specifically developed for such uses. OpenBullet is a webtesting platform that enables requests inputs against any target webapp and offers multiple tools to augment the results. This suite is used for website scraping, data parsing, automated penetration testing, unit testing in combination with Selenium and much more.
Just like Selenium, even webdriver has multiple options to choose from, for all related programming languages. For Python, if you view selenium site-package for webdriver options (C:\Users\UserName\AppData\Local\Programs\Python\Python38-32\Lib\site-packages\selenium\webdriver) you will can find that it supports multiple web drivers to work with for automation purposes, including Android and BlackBerry for mobile applications.
Incorporation of Penetration Testing in EGS Services
EC-Council Global Service(EGS) provides multiple platforms and services as part of its cybersecurity solutions that help organizations protect, detect, respond, and correct vulnerabilities and threats. EGS services are designed to better equip your security infrastructure by helping your organizations build and develop a threat-aware program that ensures the safety of your organization’s information system from intrusion. Our penetration testing services which utilizes a wide range of methodologies, helps both the tester and the organization to find vulnerabilities that are normally difficult to identify. This also includes credential stuffing, which helps the penetration tester step in the shoes of a malicious attacker to try and attack the organization’s web security to search for gaps, which upon identification could be patched by the web development and security engineers.
FAQs




