
The Risk Management in Technology (RMiT), is policy guidance formalized by Bank Negara Malaysia (BNM), effective from January 2020. The proposed guidelines are applicable to all the financial institutions listed under the accreditation of Bank Negara Malaysia, which includes local and international banks, insurers, takaful operations, issuers of e-money, and operators of designated payment systems. The aim of RMiT (Risk management in Technology) is to lay down a standard for Malaysian financial institutions (FI) to build and develop a necessary framework, policies, protocols, and security structure to manage and control the risks posed to the organization’s cyber landscape.
The RMiT (Risk management in Technology) guidelines define ‘risk in technology’ as any risk emerging from the information technology or cyber threat landscape, which could be the result of system or security failure. This implies that any vulnerability in the organization’s security infrastructure that could be exploited by internal or external forces and could lead to financial loss or disruption of financial operations is considered as a risk.
 Policy Framework Requirements
Policy Framework Requirements
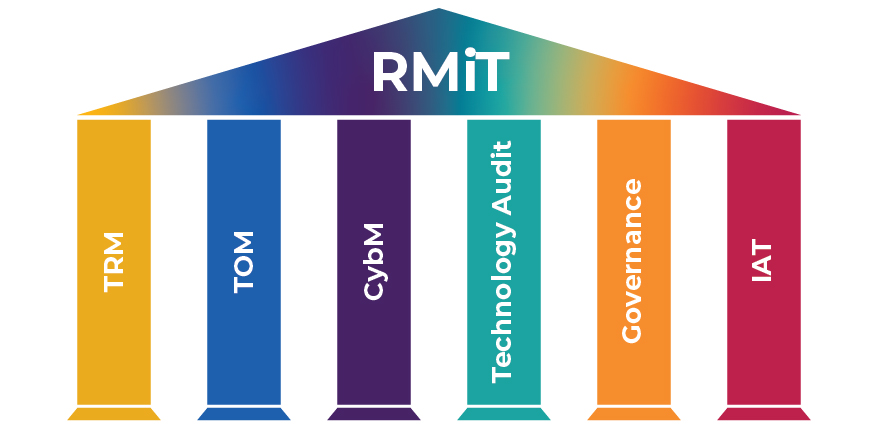
Risk management is a continuous end to end process of identification, assessment, mitigation, and monitoring. Among its policies, RMiT (Risk management in Technology) covers four technical domains of namely Technology Risk management, Technology Operations Management, Cybersecurity Management, and Technology Audit, and two non-technical regulatory domains of Governance and Internal Awareness and Training. Some of the guidelines stating the role of an organization are listed as follows:

Technology Risk management (TRM)
- Ensuring the TRM framework to be an integral part of a financial institution’s security infrastructure
- Defining of clear roles, responsibilities, risk assessment, risk classification, risk measurement, controls, mitigations, and monitoring
- Implementing the framework and technology throughout the organization
- Appointment and designation of CISO (Chief Information Security Officer) to manage risks and advising decision-makers about security matters
- Enforcing compliance with corresponding regulatory policies
Technology Operations Management (TOM)
- Establishing clear governance policies for a technology project, along with continuous monitoring and periodical review report
- Establishing an enterprise architectural framework (EAF) that describes the organization’s network, security, and technical infrastructure. EAF helps organizations conceptualize the design and maintenance of security infrastructure in compliance with their business goal
- Establishing system development and acquisition policies, and encompassing system design, development, testing, deployment, change, management, maintenance, and decommissioning for system development life cycle (SDLC)
- Encouraging implementation of automated tools for SDLC and source code review
- Establishing robust cryptography policy such as encrypting sensitive information during the exchange or transfer on external/public network
- Ensure cryptographic controls, key generation policies and certificate creation guidelines
- Establishing protocols for data center risk assessment (DCRA) such as accommodating space for data center and managing its access policies
- Establishing guidelines for data center operations along with, real-time monitoring, capacity management, activity segregation, automation, risk assessment, recovery guidelines, business continuity planning, independent assessment of end-to-end backup storage and delivery management, and availability of critical systems
- Establishing network resilience design, which includes critical network service management, network bandwidth monitoring, network design blueprint, log maintenance, network segmentation, and network resilience & risk assessments (NRA), which are to be conducted periodically or upon new changes or incorporation in the design.
- Formatting vendor service management and security guidelines for competency check, service level agreement, risk assessment, compliance status, data storage, and handling, and end of service agreement
- Defining proper protocol and guidelines for cloud service such as information migration procedure, public cloud usage protocols, risk assessment, service agreement, and end of service agreement
- Establishing protocol and guidelines for information access control which should include identification, authentication, authorization, access denial, password policy, multifactor authentication, and monitoring the user activity
- Establishing guideline for the patch for vulnerabilities and end-of-life system management
- Design, implementations, monitoring, and documentation of all the digital & technology security controls effective through across the organization, of which the authentication of financial transactions should be an important aspect
Cybersecurity Management (CybM)
- Establishing guidelines for cyber risk management which should include cyber risk framework applied throughout the organization, automated tracking and monitoring system, protection, detection, identification, and prevention strategies
- Formatting cybersecurity operation guidelines which include mitigation methods against cyber-attack lifecycle, supporting tools and software, penetration testing, and standard operating procedures for VAPT
- Establishing guidelines and protocols to conduct and incorporate, frequent compromises assessment of the system/network to detect and mitigate potential threats sitting in an organization’s digital environment
- Establishing guidelines for a Distributed Denial of Service (DDoS) attack which includes mitigation of DNS based attack, identifying and diverting malicious traffic, and expanding network bandwidth if required
- Establishing Data Loss Prevention (DLP) policies which must include data owner accountability, data classification, the data discovery process, accessibility, control procedures, and data removal policies
- Establishing SOC (Security Operations Centre) guidelines, which comprises of Security Information and Event Management (SEIM), incident response, threat hunting, threat statistics, threat intelligence involving tactics, techniques, and procedure (TTP), physical security, 24×7 operation, and threat assessment reporting
- Establishing cyber response and recovery norms, which include cyber incident response plan (CIRP), preparedness, detection, analysis, containment, eradication, recovery, and post-incident mitigation and documentation
- Appointing Cyber Emergency Response Team (CERT) to handle security incidents and collaborate with capable authorities to mitigate the threat
Technology Audit

- Ensuring the scope, frequency and intensity of technology audits are commensurate with the complexity, sophistication, and criticality of technology systems and applications
- Internal audit functions, resourced with relevant technologies and audit competencies
- Appointing professionally certified audit engineers who are adequately conversant with the developing sophistication of the financial institution’s technology systems and delivery channels
- Establishing the technology audit plan and guidelines, providing appropriate coverage of critical technology services, third-party service providers, material external system interfaces, delayed or prematurely terminated critical technology projects and post-implementation review of new or material enhancements of technology services
Governance

- Assigning roles and responsibilities to the board of directors and senior management accordingly
- Establishing and approving the technology risk appetite aligned with the risk probabilities, and approving the corresponding risk tolerances levels
- Establishing norms for key performance indicators and risk indicators, along with monitor the financial institution’s risk against its approved risk levels
- Ensuring that the senior management provides regular updates and reports on the status of the indicators along with detailed information on key technology risks
- Facilitation of critical technology operations for strategic decision-making, and oversee the adequacy of the financial institution’s IT and cybersecurity strategic plans
- Effective implementation of technology risk management framework (TRMF) and cyber resilience framework (CRF)
- Appointing a committee to provide oversight over technology-related matters, and the review technology framework for the board’s approval
- Ensuring that risk assessment to be undertaken concerning material technology application and to be submitted to the Bank
- Promoting effective technology discussions and including suggestions from technical experts
- Overseeing that sufficient time and resources are allocated to cybersecurity-related issues along with continuous engagement in cybersecurity preparedness, education, and training
- Authorizing board audit committee (BAC) responsible for ensuring the effectiveness of the internal technology audit function. This includes assessing the audit competence of staff, review of audit scope, procedures and frequency of technology audits, oversight over the prompt closure of corrective actions to address technology control gaps
- Establishing a cross-functional committee to provide guidance on the technology plans and operations
- Assess and address any deviation from technology-related policies after carefully considering related risks
Internal Awareness and Training (IAT)

- Providing adequate technology and cybersecurity-related awareness education for all the employees in accordance with their respective roles
- Measuring the effectiveness of training and education through tests or other metrics
- Conducting cybersecurity awareness and education programs periodically or at least annually, and must reflect the current cyber threat landscape
- Providing continuous training for staff directly involved in technological operations and periodically assessing the staff for competency to effectively perform their roles and responsibilities
- Ensuring continuous education for day-to-day IT operations staff, such as IT security, project management, and cloud operations
- Providing board members with regular training, awareness, information on technology developments, developing risks, etc. to enable the board to discharge its oversight role effectively
Benefits of complying with RMiT
- The incorporation of the RMiT Exposure Draft helps an organization grow and develop its cybersecurity posture among the national and international financial service institutions
- With the growing sentiment for more robust cybersecurity for financial institutes, the reputation of institutes complying with RMiT guidelines among the consumers will also increase
- Ensure that the customer data are afforded greater protection will increase stakeholder investment and reduces the risk of a breach
- RMiT related cybersecurity practices also act as a baseline for cyber insurance and legal and regulatory compliances
- The Monetary Authority of Singapore has also issued a notice on cyber hygiene which prescribe the certain level of cybersecurity practices as the threshold for hygiene standards in cybersecurity, RMiT exposure draft works in that very direction
- Experts believe that due to the mandate of RMiT many security firms will jump at the opportunity and would provide better pricing to stay ahead of their competitors, hence, saving the financial institution a major cut from the overall budget
- Studies and Reports have found that nearly 77% of consumers consider security as the third most important factor and confirmed substantial improvement in customer satisfaction (C-SAT) scores by 13% for the organizations with better security
- Reports have also suggested that improving cybersecurity can drive potential annual revenue growth of 5.4% annually
- Studies have also found that only retailers that are able to efficiently align their cybersecurity measures with customer expectations will be able to attract top-line revenue
- As a mandate of incorporating RMiT will encourage financial institutions to acquire third party assistance, hence, transferring the risk burden from the institution to vendor
Conclusion
Provided the baseline mandated by the RMiT exposure draft, financial institutions in Malaysia now need to take this opportunity to review their security posture against these guidelines and revise any existing policy that falls short of the stipulated requirement. It is very well understood that not all institutions could afford to install and incorporate major security features by themselves. Thus, approaching a third-party like EC-Council Global Services, who is well versed in cybersecurity management and provide their skills and advice as a service, is strongly advisable. Financial institutions should also begin identifying and recruiting appropriately qualified candidates for various crucial positions, given the competition for talent in this domain. Staff augmentation and outsourcing will help the institution better staffing for security technology.
FAQs




